Proactive Measures in Software Development to Avoid Critical Errors

Back to news The recent CrowdStrike outage highlights the importance of using abstract interpretation to mathematically guarantee bug-free software and ensure reliability. Key Points: Understanding Memory Access Violations: The recent software update for CrowdStrike Falcon triggered a memory access violation bug, resulting in the Blue Screen of Death (BSOD) during system startup, showcasing the dangers […]
TrustInSoft Analyzer Buyer’s Guide
Back to news Discover A New Approach to Static Code Analysis with Formal Verification TrustInSoft Analyzer Buyer’s Guide Introduction Current Market Problem / Landscape Justification Why Current Solutions Do Not Solve the Problem A New Approach to Static Code Analysis with Formal Verification Hybrid Code Analysis Required Capabilities Needed to Solve the Problem Questions to […]
Elevating Compliance with TrustInSoft’s New CERT-C Reporting

icon/arrow Back to news Reduce the risk of security breaches, decrease costs associated with late-stage bug fixes, and improve testing for industry safety and security standards with CERT-C Reporting. CERT-C Reporting Key Points Summary One-Click Compliance Reporting: Effortless generation of CERT-C standard compliance reports integrated directly into TrustInSoft Analyzer. Enhanced Standards Compliance: Seamless mapping of […]
Webinar: Mastering ISO 26262 Compliance with TrustInSoft
Back to news Accelerate the ISO 26262 compliance for functional safety with TrustInSoft Analyzer Mastering ISO 26262 Compliance with TrustInSoft In the dynamic realm of automotive software development, achieving compliance with the ISO 26262 standard is paramount for ensuring functional safety. This webinar will explore how TrustInSoft Analyzer, with its robust capabilities in fault […]
Accelerating C and C++ Testing with TrustInSoft’s Trend Reporting
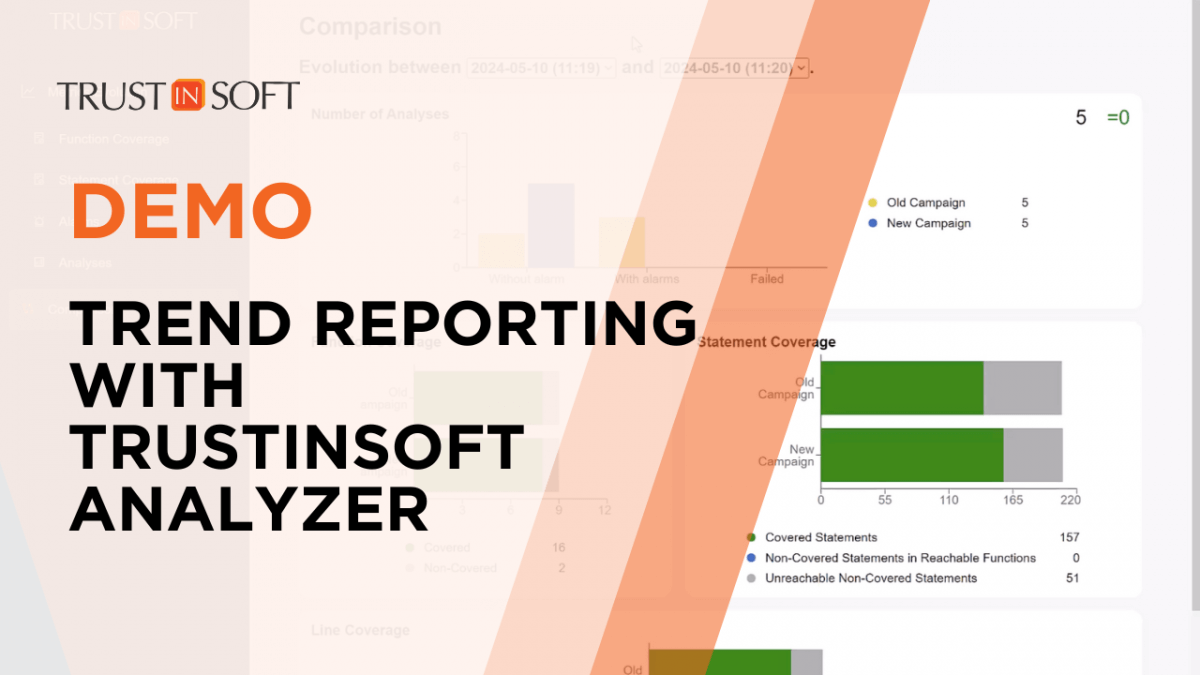
Back to news TrustInSoft Analyzer’s Trend Reporting streamlines C and C++ testing, enabling comprehensive analysis, easier progress tracking, and enhanced communication for continuous improvement. /*! elementor – v3.21.0 – 15-04-2024 */ .elementor-widget-image{text-align:center}.elementor-widget-image a{display:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:middle;display:inline-block} /*! elementor – v3.21.0 – 15-04-2024 */ .elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px} Key Highlights: Combine multiple analysis […]
Comprehensive Algorithm Testing with TrustInSoft’s Input Coverage Reporting
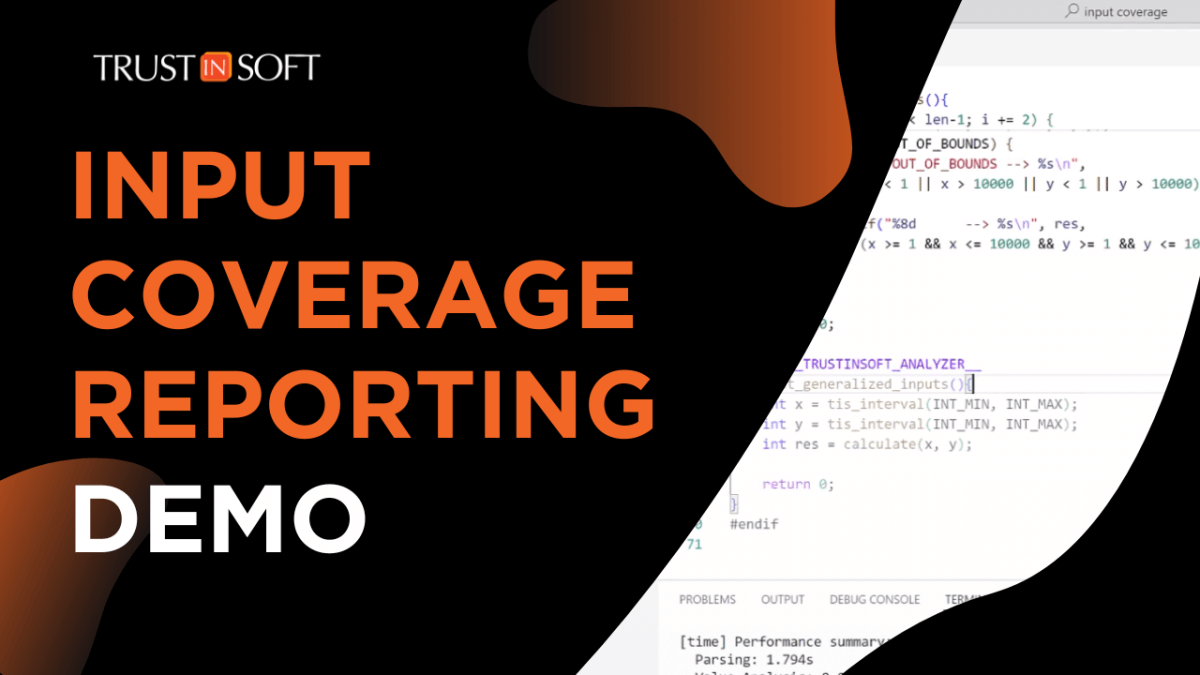
Back to news TrustInSoft Analyzer 1.47 introduces Input Coverage Reporting, ensuring exhaustive validation of all possible input scenarios while doing comprehensive algorithm testing, enhancing software safety and reliability. /*! elementor – v3.21.0 – 15-04-2024 */ .elementor-widget-image{text-align:center}.elementor-widget-image a{display:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:middle;display:inline-block} /*! elementor – v3.21.0 – 15-04-2024 */ .elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px} Key […]
TrustInSoft AUTOSAR Integration Enhancements
Back to news TrustInSoft integrates AUTOSAR standards and formal methods to enhance software reliability, and reduce development time and costs, making it a vital partner in the evolving automotive industry landscape. TrustInSoft AUTOSAR Integration Enhancements Key Points: Enhanced AUTOSAR Integration: Simplify AUTOSAR development by automatically processing ARXML files, generating analysis assets, and feeding them directly […]
How to Perform Large-Scale Software Testing with TrustInSoft Project Manager
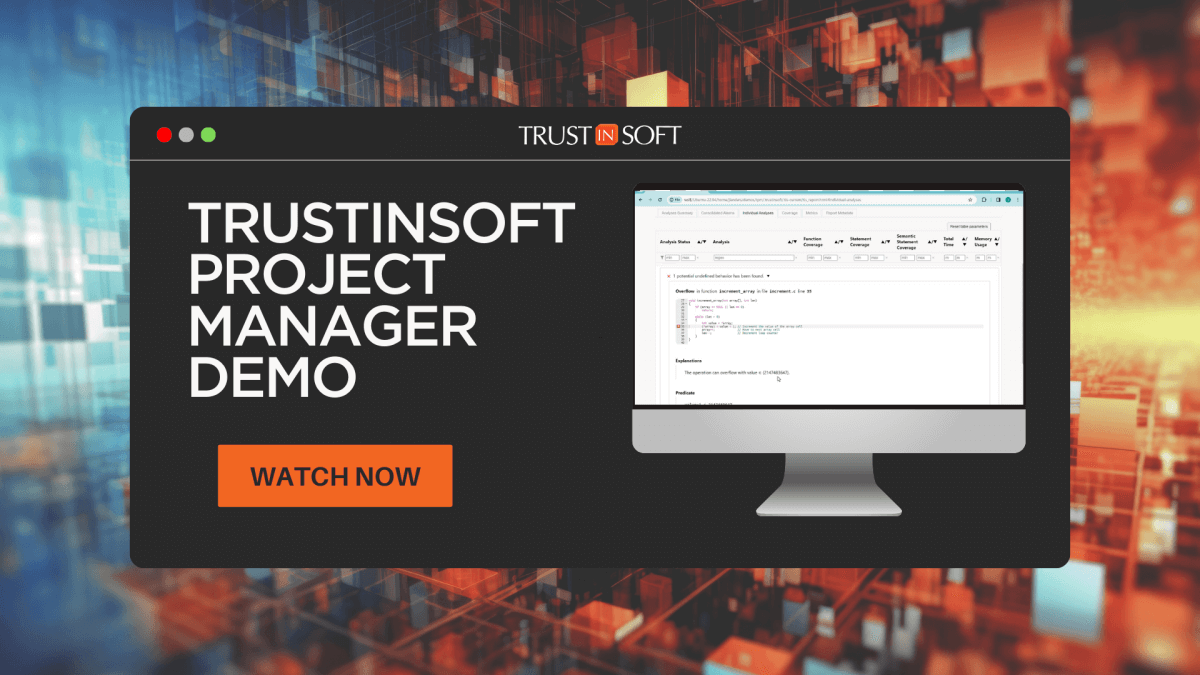
icon/arrow Back to news The comprehensive solution designed to enhance the efficiency and effectiveness of your software testing campaigns TrustInSoft Project Manager Key Points: Efficient Setup: TrustInSoft Project Manager simplifies the configuration of large-scale testing campaigns, allowing for seamless setup and execution. Scalable Testing: Designed to handle complex software testing environments, it ensures comprehensive analysis […]
Embedded World 2024 Recap

Back to news TrustInSoft launched TrustInSoft Analyzer 1.47 including new ease of use and enhanced report features at Embedded World 2024 /*! elementor – v3.21.0 – 15-04-2024 */ .elementor-widget-image{text-align:center}.elementor-widget-image a{display:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:middle;display:inline-block} /*! elementor – v3.21.0 – 15-04-2024 */ .elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px} Zero Bug Software at Embedded World 2024 […]
Announcing TrustInSoft Analyzer 1.47: Elevating Software Development to New Heights
icon/arrow Back to news Streamline your workflow, ensure compliance, and provide the insights you need for successful project outcomes. Elevating Software Development to New Heights In the fast-evolving world of software development, efficiency, reliability, and compliance are not just goals—they are necessities. TrustInSoft is at the forefront of ensuring that businesses achieve these essentials through […]