CERT C Compliance with TrustInSoft Analyzer

Improve Code Safety, Reliability and Security with CERT C
TrustInSoft Analyzer provides exhaustive static analysis to ensure your C/C++ code adheres to the CERT C coding standard, minimizing vulnerabilities and enhancing software security. Trust our analyzer for unmatched precision and comprehensive coverage of all CERT C rules to achieve CERT C compliance.
Book a Demo
Exhaustive Detection and Elimination
TrustInSoft Analyzer detects and eliminates undefined behaviors, ensuring zero critical bugs. With 100% input coverage, our tool guarantees the absence of vulnerabilities, making your software robust and secure.
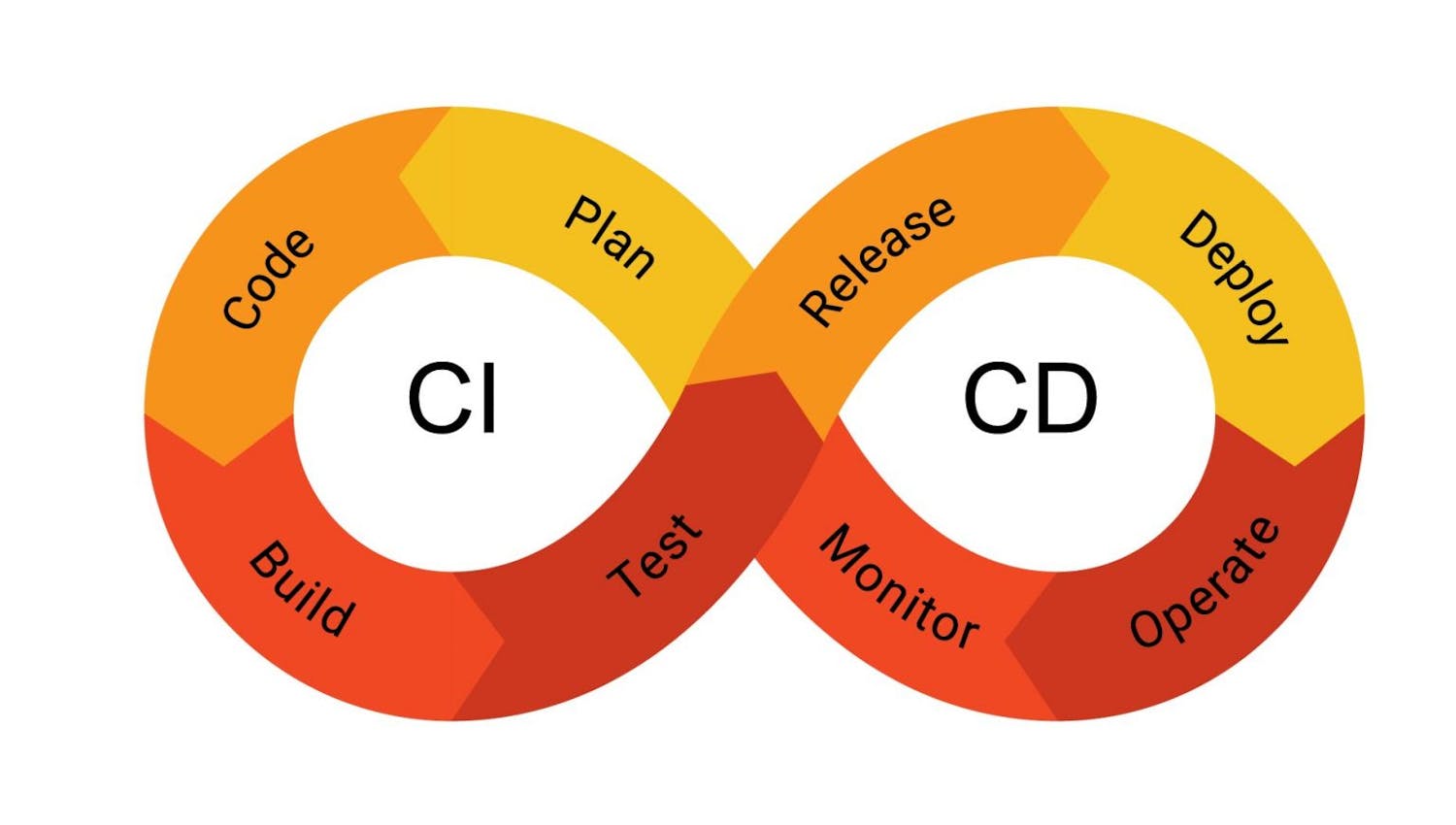
Seamless Integration and Efficiency
Integrate TrustInSoft Analyzer seamlessly into your development workflows for CERT C software verification. By automating code analysis, developers can reduce debugging time and increase productivity, all while ensuring compliance with CERT C standards

Mathematical Guarantees and Reliability
Achieve mathematical certainty with TrustInSoft. Our analyzer provides formal proof of software reliability and security, helping you meet stringent industry standards and reducing the risk of costly security breaches.





