The High Cost of Low-Quality Code: Cost of a Bug throughout the SDC
January 7, 2025
The Cost of Software Defects
Key Points
- The longer you wait to address bugs in your code, the more costly the fix. Bugs on the field can be more costly than money in terms of brand reputation.
- Shifting left in the software development cycle (SDC) improves the speed of detection of memory safety vulnerabilities.
- You can reduce the risk of buggy software by going beyond static analysis with an exhaustive and sound hybrid analyzer.
Proactiveness in Software Development
Security starts with the low-level embedded software layers typically powered by efficient languages such as C/C++. It is critical to secure this software to help prevent issues like DOS attacks and program crashes caused by integer overflows, buffer overflow, illegal memory access and other memory safety vulnerabilities.
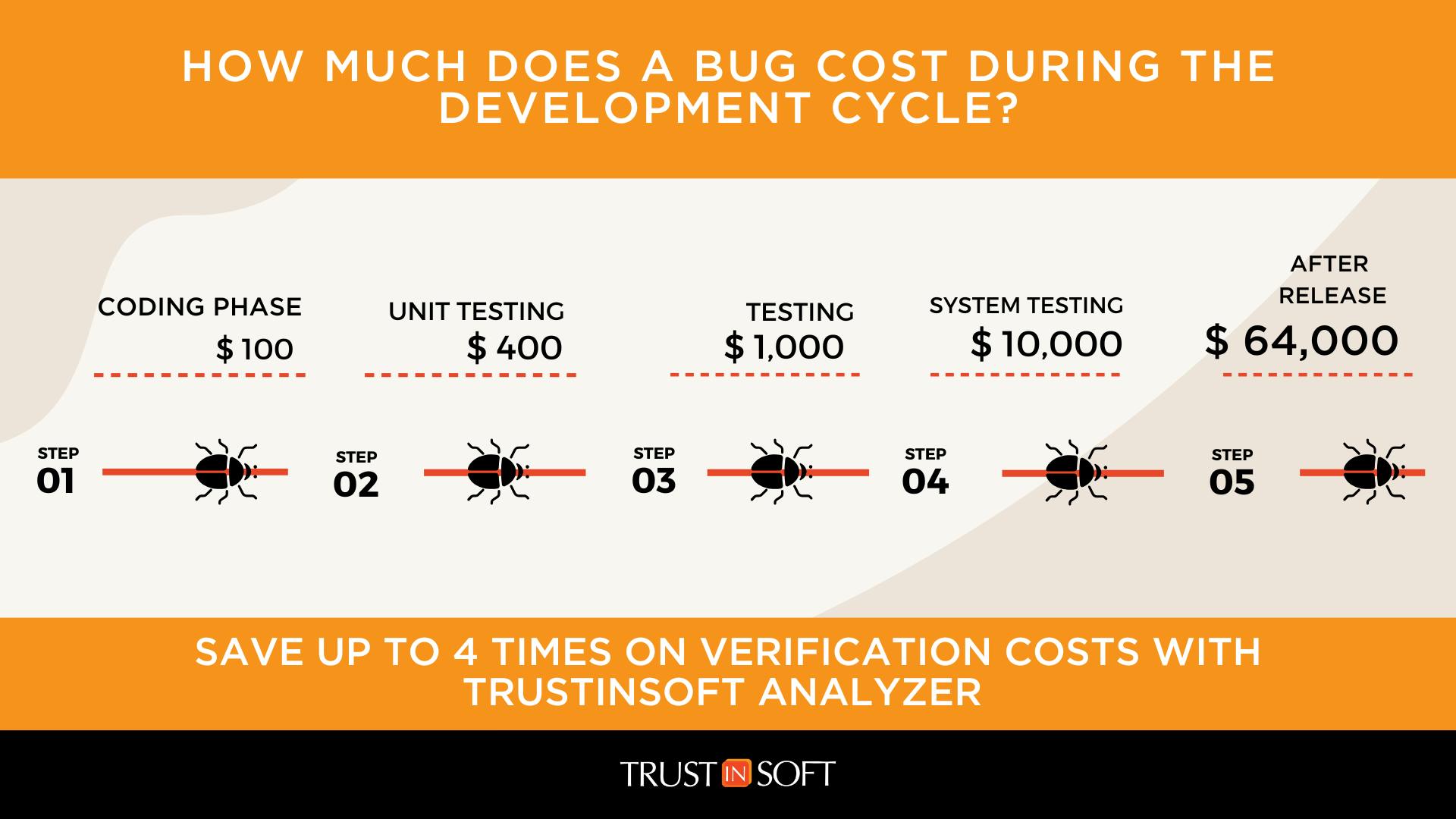
Finding bugs in each stage of the Software Development Cycle
At every stage of the SDC, bugs have a cost. This cost increases exponentially the further the bug travels through the software development cycle.
In the coding stage, a bug might cost the price of developer time to rework the logic of the code and improve it before sending it off to the next development stage.
During unit testing, the time of testers can be extended. Legacy solutions miss vulnerabilities because they only have the ability to check some of the possible scenarios. Sound and exhaustive static analysis tools like TrustInSoft Analyzer approach the problem differently. They can ensure that no critical memory vulnerabilities such as memory leak or buffer overflow, are not examined. It explores and exhaustively checks an infinite number of possible scenarios. This allows you to zoom in and confidently catch bugs earlier in the process.
Next is further general testing and verification: At this point, more rework is required to fix bugs identified during this stage. The fixes may require significant code changes and are more costly and time-consuming to resolve.
Finally, during system testing, the software must be tested with the hardware. Consequently, the cost of fixing and reworking significantly increases. At this stage, and even earlier significant problems can delay the release of the product, which has an impact on the revenue or certain market opportunities.
Once the software has been released, the cost of a bug can go up to $64,000 or more, depending on the product, industry and scope. This does not even include potential rework, possible recalls, onsite maintenance, or customer support costs. Certain bugs can also compromise the security and privacy of their users, which may expose them to even larger problems with regulatory bodies. For especially severe violations, listed in Art. 83(5) GDPR, the fine framework can be up to 20 million euros, or in the case of an undertaking, up to 4 % of their total global turnover of the preceding fiscal year, whichever is higher.
Beyond the obvious financial costs, there are indirect costs including reputational damage and loss of productivity. These are seen after manufacturing in the brand image and time-to-market sensitive opportunities that can be lost if the timing is not right.
Bug Bounties
The price of a bug can go much higher than that for certain organizations. Several companies host bug bounty programs that reward white hat hackers for reporting vulnerabilities in their software.
Google’s bug bounty program pays up to $151,515 USD. This implies that the cost of a bug depends on the context of the software, the industry, and the organization. In a connected world that depends more and more on software in daily operations, leaving vulnerabilities in the code is more and more costly the further in the SDC. This has incentivized organizations to proactively work with ethical hackers to identify vulnerabilities in their software for an award, thus contributing to the monetary value of certain vulnerabilities
Not all bugs are created equal (look out for CVEs)
CVEs are Common Vulnerabilities and Exposures, they belong to a group called CWE (Common Weakness Enumeration). They are reported on the MITRE website and often include dangerous memory safety vulnerabilities that are difficult to test using traditional static analysis. Some of the CWE Top 25 include vulnerabilities known as undefined behaviors. These can include buffer overflow, use-after-free, null pointer deference, signed (integer) overflow, and more.
Shift left with TrustInSoft Analyzer
Using abstract interpretation-powered tools, developers can test partial verification using just the code and input values without an additional formal specification. This empowers developers to embrace the power of formal methods without extensive experience.
Developers are empowered to shift left in the development cycle with the ability to run mathematical guarantees on their own test suites and test abstract values for input generalization at the source code level.
TrustInSoft Analyzer integrates into your existing CI/CD processes and helps you to emulate the target hardware for more accurate testing sooner in the process. You can start by perfecting your unit tests and move into sound and exhaustive analysis with automated abstract interpretation to increase speed and coverage of all possible values used by your software.
Reduce the Risk
Some other best practices to minimize the cost of buggy software such as:
- Effective Bug Tracking and Management
- Security Auditing
- Consistent developer training
- Comprehensive and robust testing
- Code Review
Coupling best practices with efficient testing tools significantly reduces the risk of a costly bug slowing down the SDC. Automate time-consuming tasks such as code review with exhaustive static analysis. TrustInSoft Analyzer can mathematically prove your source code’s safety, security, and reliability.
Request a demo to understand how TrustInSoft Analyzer can identify key memory safety vulnerabilities.