Deliver stable and vulnerability free software
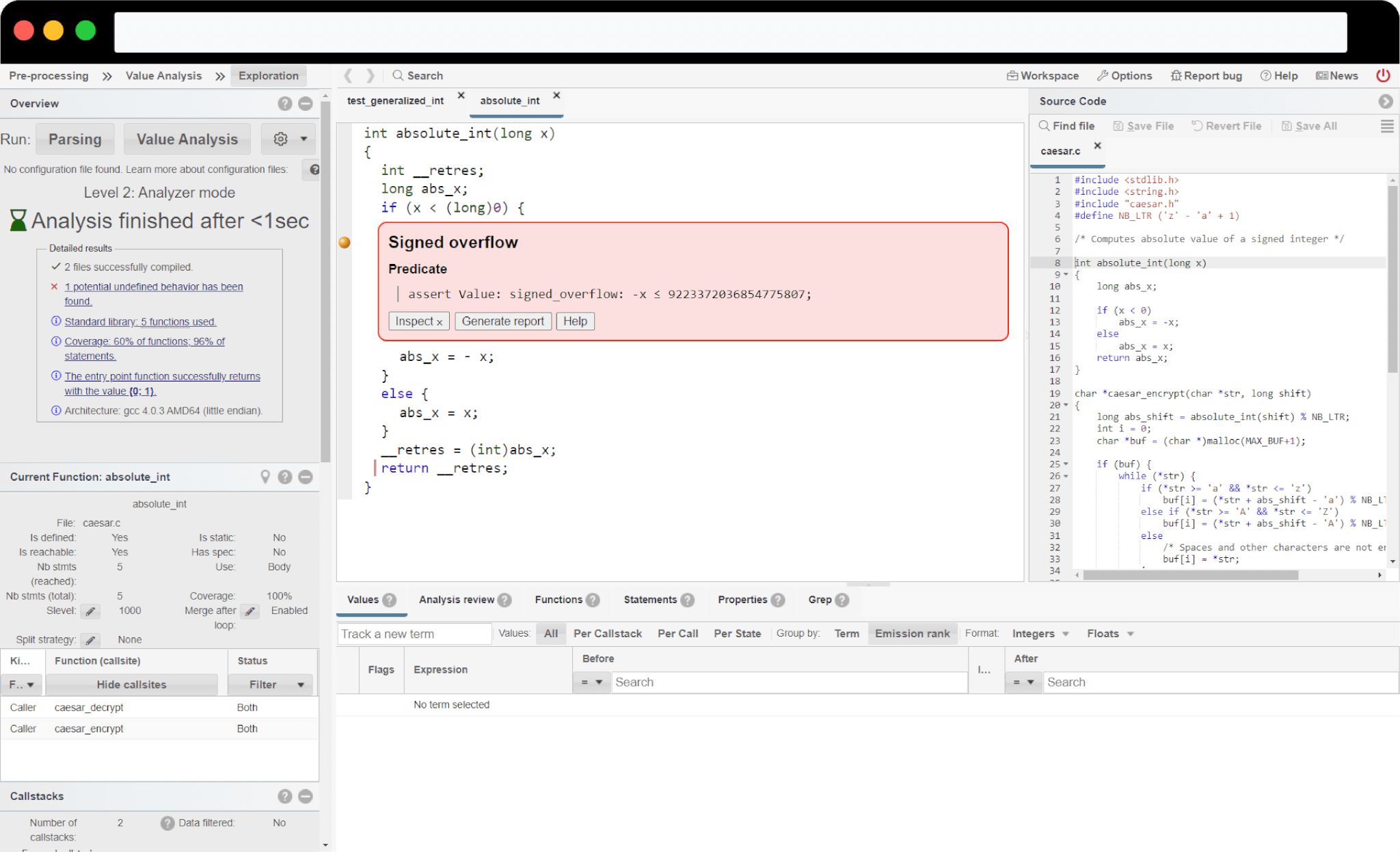
Recognized by the NIST, TrustInSoft Analyzer goes further than any other static analysis tool by focusing on the semantics of the code, rather than syntax, using formal methods. TrustInSoft Analyzer mathematically proves the absence of even the most hidden bugs and integrates easily in the CI process.
Supercharging existing unit tests to detect more bugs than standard tests
Generalizing tests to exhaustively detect C/C++ language vulnerabilities
Checking functional implementation to ensure program behaviors are compliant with their specifications
TrustInSoft Analyzer identifies all bugs, resulting in no false negatives, no false positives, meaning each bug is real and needs to be corrected.
TrustInSoft Analyzer boosts the coverage of your tests by generalizing inputs, allowing you to test the superset of possible values for an exhaustive coverage of your code.
TrustInSoft Analyzer uses a series of formal methods to mathematically model your code, allowing you to obtain a mathematical proof that there are no bugs left once all issues detected by TrustInSoft Analyzer are corrected.

TrustInSoft Analyzer allows you to reduce software test coverage costs, optimize bug identification and remediation, and prioritize bug correction.

Using TrustInSoft Analyzer on your software source code allows you to position safety and/or security as a feature to gain market share or price premium, achieve a certification level, and secure Time to Market sensitive opportunities.

TrustInSoft Analyzer helps you reduce field support costs post-production and avoid brand or image valuation impacts due to buggy code.

TrustInSoft is recognized by the National Institute of Standards and Technology (NIST) for its ability to prove the absence of entire families of bugs.
TrustInSoft’s clients use TrustInSoft Analyzer to develop safer and more secure products. Read about their experiences using TrustInSoft Analyzer here!
Recognized by the NIST, TrustInSoft was founded in 2013 by three former researchers of the The French Alternative Energies and Atomic Energy Commission. Today, TrustInSoft supports international customers in a variety of industries, including aeronautics, telecommunications, industrial IoT and automotive.
